What is security?
The world has become more modern, developed and connected with the invention of the internet, But at the same time it also has become a dangerous threat to many people as well for which Security has become the fundamental need for web application, websites and more. Security, a concept that is used from early ages.
Let’s explore what security means. Security is the use of preventive measures against attacks, unwanted access, and damage to software, data, and systems. Writing code is not enough; you also need to write code that can pass the tests that possible dangers might throw at you. Even in early ages we used to hide things so that it does not get stolen or harmed by anyone.
Security is a protection from any unwanted threat to any data. Securing only data is not sufficient. Sometimes you want to secure business logic as well, for this java has an amazing framework, Spring security that saves tons of developer time and also provides the best security to the program.
Why Is Security Important?
Since cyber threats are so common in the digital world, programming security is more important than ever. Data breaches and other disastrous outcomes, including monetary losses, business logic might result from a security breach. The barrier that protects data and system availability, confidentiality, and integrity in programming is called security. Spring Security provides many functionalities to protect your data, business logic from these cyber attackers. Securing your application is important to protect your users sensitive data from cyber attackers that can use it for illegal activities and to not break the trust that the user have placed when using your application.
Understanding CORS.
CORS short form for Cross-Origin Resource Sharing is a type of security layer provided by a browser. Many misunderstand CORS as a cyber attack but it is a type of security layer present
in most browsers. CoRS is a protocol that allows scripts to communicate with resources from an alternate origin while they are executing on a browser client. For instance, CORS would prevent
a UI application from calling an API that is operating on a different domain by default. The majority of browsers implement this W3C specification.
So Cors is not a security issue/attack but the default protection provided by browser to stop the data/ communication between different origins.
“Other Origins” means the url being accessed differs from the location that the JavaScript is running from, by having
- a different domain
- a different scheme(HTTP or HTTPS)
- a different port
Solution to handle CORS
In a valid scenario where Communication is necessary, The @CrossOrifgin annotation can be used to permit certain types of interactions, such as those that occur when a Web App UI that is
deployed on one server tries to connect with a REST service that is installed on a different server. The API can be used by clients from any domain thanks to @CrossOrigin.
@CrossOrigin annotation can be mentioned on top of a class or method like below:
@CrossOrigin(origins= “http://localhost:4200”) //this will allow on the specified domain
@CrossOrigin(origins= “*”) //this will allow on any domain
Another way of resolving this is by defining CORS related configurations globally using Spring Security
for example:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
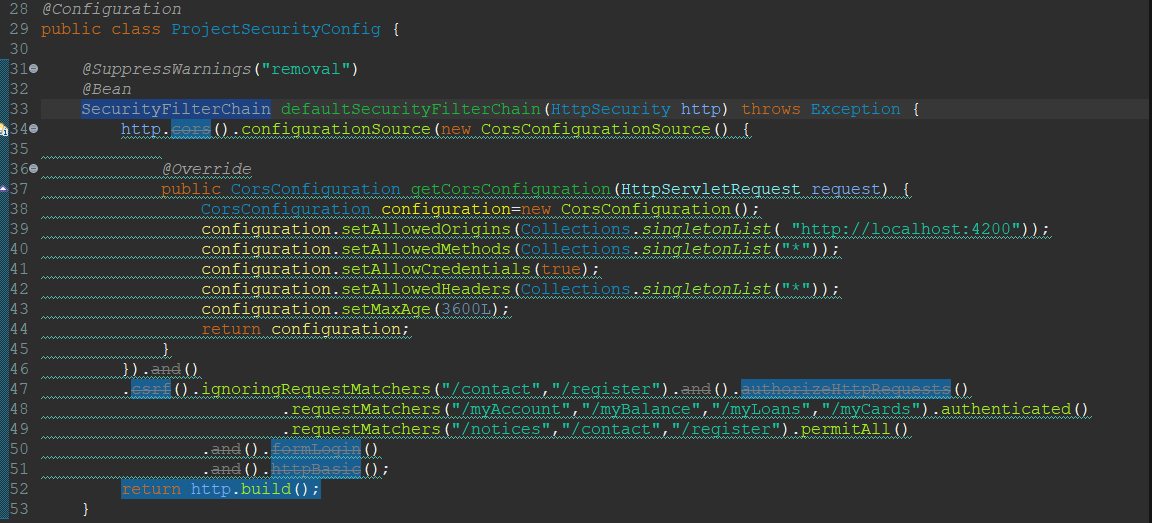
@Configuration public class ProjectSecurityConfig { @SuppressWarnings("removal") @Bean SecurityFilterChain defaultSecurityFilterChain(HttpSecurity http) throws Exception { http.cors().configurationSource(new CorsConfigurationSource() { @Override public CorsConfiguration getCorsConfiguration(HttpServletRequest request) { CorsConfiguration configuration=new CorsConfiguration(); configuration.setAllowedOrigins(Collections.singletonList ( "http://localhost:4200")); configuration.setAllowedMethods(Collections.singletonList("*")); configuration.setAllowCredentials(true); configuration.setAllowedHeaders(Collections.singletonList("*")); configuration.setMaxAge(3600L); return configuration; } }) |
By configuring The CORS. We can allow communication between different domains, ports and schemas.
Use this code in the SecurityFilterChain type of bean.
CSRF or CROSS-SITE REQUEST FORGERY
It is a type of cyber-attack on your application. A common Cross-Site Request Forgery(CSRF or XSRF) attack that seeks to perform an operation in a web application on behalf of a user without
their will.
For example:
Think it like you are using a website called primevideo.com and the attacker’s website hacker.com
1 When a user logs into primevideo.com, the website’s backend server sends a cookie to the user’s browser, which is stored against the Primevideo.com domain.
2 The same user opens a different tab in the same browser and visits the website hacker.com.
3. A malicious link to change the email associated with a Primevideo account is embedded in the webpage that Hacker.com returns. However, a link that reads “90% OFF on iPhone” displays.
4 The malicious link that the user was tempted to click on led to a request to primevideo.com. Because the login cookie was already set up in the browser and the request to modify email address was sent to the same domain, primevideo.com, the backend server of Primevideo was unable to determine the source of the request. In this case, hacker.com faked the request to appear as though it was made from a primevideo.com user interface page.
5 Due to a request sent by hacker.com, the primevideo user’s email will be changed.
For example the request will look something like this:
|
1 2 3 4 5 6 7 |
<form action="https://primevideo.com/changeemail" method="POST" id="form"> <input type="hidden" name="email" value="user@hacker.com"> <form> <script> document.getElementById('form').submit() </script> |
Solution for CSRF Attack
An application must be able to identify whether the http request is being created by the program’s user interface in order to prevent this kind of cyberattack. CSRF tokens are the most effective means of accomplishing this. A secure random token called a CSRF token is used to prevent CSRF attacks. For the token to be difficult to predict, it must be huge and random, and it
must be unique for each user session.
The steps in the procedure are as follows:
1 Once a user logs in to primevideo.com, the PrimeVideo backend server sends a cookie containing a unique, randomly generated CSRF token, which will be saved in the browser for that specific session against the Primevideo.com domain. CSRF token is inserted within hidden parameters of html forms to avoid exposure to session cookies.
2 The same Primevideo.com user opens a new tab in the same browser and visits Hacker.com.
3 hacker.com returns a web page with a malicious link with the text “90% OFF on iPhone” embedded with a request that allows the attacker to modify your PrimeVideo account’s email address
4. The link makes requests to Primevideo.com. Since the login cookie is available in the browser and the request to update the email is being made to the same domain Primevideo.com. This time, the Primevideo.com backend server expects a CSRF token with the cookies. The initial value generated during the login process must match the CSRF token
5. this will not let the hacker change the email and get a error 403 from Primevideo Spring Security allows the developer to implement and configure CSRF in their application easily.
To configure CSRF in your Spring application use the below snippet:
|
1 2 3 4 5 6 |
.csrf().ignoringRequestMatchers("/contact","/register").and().authorizeHttpRequests() .requestMatchers("/myAccount","/myBalance","/myLoans","/myCards").authenticated() .requestMatchers("/notices","/contact","/register").permitAll() .and().formLogin() .and().httpBasic(); return http.build(); |
Use this code in the SecurityFilterChain type of bean.
Conclusion
Security has become a most crucial part of any application. Spring Security helps developers to implement security in their program and prevent cyber attacks such as CORS & CSRF by providing us with functionality that can be easily configured according to the user’s needs. Practice of Security is a production need in today’s time. This article has covered the fundamentals of programming security, highlighting its significance and offering advice on how to protect the code against attacks.













Deepak Prajapati
2024-01-25